Insurance Australia Group (IAG) has started working on ways to make its software engineering functions more AI driven, beginning with…
Flashpoint has long been known for its industry-leading data collection and finished intelligence. After two major acquisitions in 2022, we…
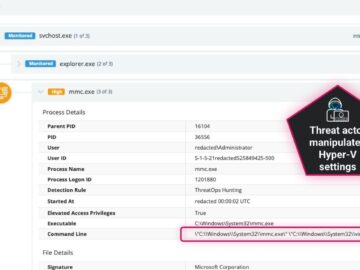
Hypervisors are the backbone of modern virtualized environments, but when compromised, they can become a force multiplier for attackers. A…
Russian state-sponsored hackers have been linked to an ongoing Signal and WhatsApp phishing campaign targeting government officials, military personnel, and…
A red teamer operating under the handle OtterHacker has publicly released M365Pwned, a pair of WinForms GUI tools designed to…
If you have been using Signal or WhatsApp for work, you might want to double-check your security settings. On Monday,…
Anthropic has filed a lawsuit to block the Pentagon from placing it on a national security blacklist, escalating the artificial…
Security awareness training (SAT) is supposed to make companies safer, but too often, it feels like just another box to…
Hackers contacted employees at financial and healthcare organizations over Microsoft Teams to trick them into granting remote access through Quick Assist…
Microsoft has introduced Copilot Cowork, a new AI-powered feature embedded within Microsoft 365 that moves beyond conversational assistance to autonomous…
Russian-backed hackers have launched a global cyber campaign to gain access to Signal and WhatsApp accounts used by officials, military…
Download the full report The 2026 State of Security report provides comprehensive analysis of each threat domain, threat actor profiles,…